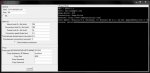
PyLoris Denial of Service Web Testing v3.0 in the wild
PyLoris is a tool for testing a web server’s vulnerability to a particular class of Denial of Service (DoS) attacks. It uses the Slowloris method; by using all available connections, web servers cannot complete valid requests.
PyLoris is a scriptable tool for testing a web server’s vulnerability to Denial of Service (DoS) attacks which supports SOCKS, SSL, and all HTTP request methods. It uses the Slowloris method.
Changes
- Tkinter based GUI for attacks
- Multiple concurrent attack support
- ScriptLoris class for easy extension and prepackaged attack creation
- libloris module providing attack API
- Intelligent Thread & Exception Handling
- Supports options to be pulled from files
- ScriptLoris class for easy extension and prepackaged attack creation
- Highly configurable HTTP connection consuming DoS
- HTTPS support
- GET, POST, HEAD and other headers supported
- SOCKS4 and SOCKS5 proxies supported
- Written in Python
- Cross Platform; supported on Windows, Linux, and Mac OS X
- Forging Referer header for severs inaccessible directly
- Gzip encoding to test for CVE-2009-1891 vulnerability
- Many more bug fixes!
Using PyLoris
Using PyLoris is simple. In its most basic form, PyLoris merely needs a copy of Python 2.6 or 3.x.
On a Linux machine, one must simply invoke the script in a terminal, stating a site to test:
- motoma@rocksalt:/home/motoma$ python pyloris-2.0.py motomastyle.com
On Mac OS X, one invokes PyLoris the same way. Using the Terminal Application:
- hotdog:/Users/Motoma/ motoma$ python pyloris-2.0.py motomastyle.com
Post scriptum
Related Articles
| Attack |
|
| Configurations checks |
|
| PyLoris |
|