Security Ninja security tool announcement
Security Ninja blog : The tool is the result of me thinking about writing a tool to help people conduct security code reviews for over a year. I had conference presentations to prepare, certification exams to sit and of course a lot of conference speaking slots last year which meant the tool idea had to go on the backburner. The benefit of having this idea going around in my head for so long is that I knew exactly what I wanted the tool to look like and how I wanted it to function before I wrote a single line of code.
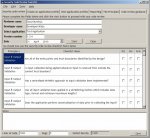
I’m writing the tool to help people perform security code reviews; it isn’t a code review tool like the OWASP Orizon or Codecrawler tools and it won’t do the static analysis or keyword matching for you. The tool will help application security professionals conduct manual security code reviews in a repeatable manner by following the same set of checklist items for every application they review. The checklist items were published on this blog in December and January so some of you will already be familiar with them. The tool will allow you to follow the checklist approach in a more professional and audit-able manner than you can using “Word document checklists†.
The tool will force the reviewer to create an application profile for any application they wish to review. This idea was inspired by the Application Security Portfolios blog post that Nick Coblentz published in 2009. The application profiles will hopefully force the reviewer to really think about the application they are reviewing and not just treat the review as lines of code that need to be reviewed. The profiles should make the reviewer think about the business impact of a vulnerability in the application being exploited, what data could be stolen and ultimately what is the real risk associated with any failure items found during the review. I hope the profiles force reviewers to realise that not all bugs are equal and ultimately produce more accurate security code review reports based on risk and not FUD.
Stay tuned we will inform you as the tool is released to public.
Compliance Mandates
|
Related Articles
| Code Auditing |
|