GFI LANguard N.S.S 8.0 Review
This is a security-database’s review of the latest release of GFI’s software LANguard Network Security Scanner 8.0. It comes with a bunch of new professional features that make vulnerability mapping and patch management easier and faster.
Introduction
We have read recently an interesting article on a security blog somewhere in this wide net-world. It said clearly that IT security officers fear the internal disgruntled (evil) users attempts to compromise vital systems more than outside attackers. This is not a new story; it is always being the case.
Maybe you have also heard in the news that many big companies suffered from a huge loss of data as well as credit cards numbers, employees’ records and other piece of sensitive information.
Amazingly, the most exploited vulnerabilities were the easiest to identify and to fix it (unpatched breaches, default or common passwords, use of unprotected storage). In other word, attackers know how to take advantage from the weaknesses related by the vulnerability laws (half-life, prevalence, persistence, focus, window of exposure and exploitation).
No matter what they say, no matter what we (security consultants, auditors, security software vendors) do; Organizations and companies do not perform enough awareness and assessment campaigns of their exposure. Not even pay attention to keep up-to-date with the latest hotfixes or overall correctly the patch management process.
One tip we personally recommend to all our customers just after an IT assessment:
“Focus on recurrent security audits sessions with a little help from a complete solution to identify, manage and fix the critical gaps and discrepancies.â€
++++
Setup
Installation
The setup of LANguard NSS 8.0 is very simple and painless. Few interactions are required:
- An account administrator is asked for the NSS service to perform scheduled tasks.
- A selection of the results database (SQL or MSDE)
- Administrator’s email is asked for sending alerts and other triggered alarms
The interface
Those who stick on old LANguard releases (2.x, 3.x) will be incredibly surprised at first glance. The new version looks very complex with a lot of tabs, windows and tree views. Sure, LANguard is not a software for script kiddies and push-button crackers. We are miles away what NSS looked years before.
The first time we tested the beta release we have said, NSS looks professional.
But take it easy. You should take time to understand how things work, and suddenly everything will become much simpler.
We will not explain all menus of the GUI interface; you have to discover it yourself. Take your time, there are a lot of options and configurations. Otherwise, we recommend you to read NSS User Guide, which is well documented, or ask for a live demo if GFI has local reseller in your country.
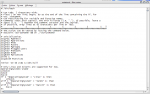
During this review, we focused on what behind the GUI interface. As security consultants from the old days, we even prefer the command line flavor and this is the beauty and strength of LANguard NSS 8.0.
First Steps
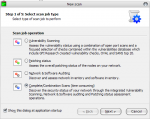
Instead of going on refining profiles that NSS ships with, we tried the wizard ,by clicking on New Scan, which guides us in 5 steps through creating an appropriate scan job.
You have the choice among 4 operations:
- Vulnerability scanning
- Patching status
- Network and software Auditing
- Complete/Combination scans (it is a time consuming option)
With each operation comes a list of profiles. Each profile has a special and dedicated aim (system information, port scanner, TOP SANS 20 vulnerabilities, SNMP audit and so on…)
When done, you are asked to select the target (from single computer to a large domain of servers and systems).
The last step is about the credentials. The audience target of this software is very specific. In order to grab useful information about the security level of the target, you should be “Domain administrator†or have privileged SSH account (in the case of Unix boxes).
As you see, it was so easy to perform a security assessment.
Scanning with built-in profiles
At least 24 profiles have been added with the last release of GFI LANguard. Each profile performs certain tests starting by a simple ping probe to full protocols scanning.
Just select the appropriate profiles along with the credentials and click on “Scan†.
NSS will, in major case, perform some implied rules (OS detection and system information).
The results are displayed in real time. We don’t even wait to the end to discover that you have missed critical patches.
Patch management and deployment
This is by far one of the greatest advantages of LANguard NSS. With just a simple click, system administrator will turn this security software to a real patch management tool.
According to the corporate security policies, you can choose either downloading the missed patched directly from Microsoft or from a repository (directory somewhere on a shared administrative disk or from a WSUSContent folder).
At this point, you will realize that GFI LANguard is more than a security scanner but a powerful all-in-one security product. Few softwares offer this ability to identify, manage and fix security gaps.
However, we recommend you to really take time to understand the patch deployment process.
This task should be performed by a qualified system administrator in compliance with your Patch Management Process.
As security consultants, we are very lazy because we always want to install and control remotely softwares or our custom packages. Imagine, you have to deploy a new release of your corporate application or a handmade tool in some servers. GFI offers this ability to do so.
Using the “Deploy Custom Software†option, you will be able to add the software to be deployed on specific computers (they should be scanned before) with options (warning users, managing service, rebooting the remote computers…).
Reporting
All your past and actual scans are stored in the database you chose during the setup stage. So that’s why you should not be worried about what you scanned 3 months ago. Everything is kept.
By clicking on “Results filtering†, you should browse among a bunch of filters (Full report until Non-Updated Security Software). The “on the fly†generated report is based on the built-in LNSS reporter and could be exported to HTML, TXT, XML or even PDF (you have a PDF printer) format.
We like the full report. Nevertheless, for advanced views and executive reporting, GFI recommends a separate package called GFI ReportCenter. This is another story and it is appropriate for large networks.
Reports generated by ReportCenter pack are professional and could supply the corporate dashboard with some options like Network Vulnerability Trend. This illustrates how security gaps changed over a given time.
The patch management status indicates using colorful charts the results of hotfixes deployment on network.
ReportCenter could be a great help to supply corporate (with large networks) Security Dashboard.
++++
What we really like ine LanGuard NSS
The wide vulnerability database
We were really impressed by the wide knowledge database that incorporates various misconfigurations checks:
- Vulnerabilities checks classified by category
- DNS
- FTP
- Software
- Web
- Rootkits
- And more
|
Integration of OVAL checks
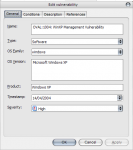
GFI LANguard NSS earns an OVAL certification. This means that the software is compliant (Open Vulnerability Assessment Language) according to the OVAL framework checks.
As a far as we can remember, LANGuard NSS have always used the “conditions†testing technique, so, it was then easy to get OVAL compatible.
However, we recommend you to be familiar with the OVAL framework (http://oval.mitre.org)
The Unix scripts
GFI have written some good scripts to asset UNIX boxes (Sun, Linux and Mac). The scripts grab information as well as :
- General info
- Partitions
- Users
- Groups
- Logged users
- Network info
- USB info
- Processes
The good part here is that LANguard NSS 8.0 retrieves these information using different advanced techniques. Indeed, I took time to read “osdata.sh†script (/Data/Scripts/). And it happens to look that many functions have been integrated using python, Perl and awk in order to avoid that old annoying message “ Command not found†.
The UNIX scripts are remotely (script sent via ssh) executed in a temporary directory with the SSH private key (note that you should be root). The directory is cleaned when tests are over.
Open minds and advanced users
GFI offers the ability for advanced system administrators and security professionals to add, modify scripts and checks.
The “Add vulnerability†lets you design a complete check process using the same OVAL (test conditions with operators) philosophy.
Whishlist: What we want to see in LANGuard NSS
Here are some topics we want to see improved or added for next coming releases into LANGuard NSS (if possible):
- Import and manage Nmap scans. The scan engine used with LANguard sometimes fails to report open protocols.
- Rely on fingerprinting Nmap database for OS identification
- The use of CVSS for scoring vulnerabilities
- Integration the use of SCAP XCCDF framework (NIST Checklist)
- The use of new profiles as well as ISO17799 compliance, COBIT Compliance.
- The Web scanning (application based) should integrate the OWASP methodology, or at least rely on a good framework to do so (nikto for example).
++++
Targets, scenarios and test cases.
During our tests, we have used these materials and software.
| TARGET | SECURITY STATUS |
|---|---|
| Windows XP Server | Patched with latest security patches. |
| Windows XP Server 2 | Unpatched (missed latest critical updates). No firewall. No antivirus. |
| Windows Server 2003 | Patched (missed some old critical patches) |
| OSX iMacG5 | Unsecured (a lot of protocols opened for test) |
| OSX PowerBook G4 | Patched and secured (this is my work machine) |
| Sun Solaris 8.0 | Patched (but a lot of protocols opened). 1 very critical vulnerability left (Oracle) |
| HPUX 11.x | Hardened server |
| iSeries AS/400 | Unsecured (a lot of protocols, shares….) |
| Ubuntu 6.10 | Unsecured |
| Security-database.com | Secured (hope it is) |
| Complete network | Large farm of windows and network devices (mainly windows 2000, Cisco IOS) |
| SOFTWARES | VERSION |
|---|---|
| N.S.S LANguard | 8.0 with the latest updates |
| ReportCenter | Pack ReportCenter 3.5 |
| Nmap | 4.20 (For TCP/UDP scans comparison) |
| SCENARIO | VERSION |
|---|---|
| Basic account | Scan Windows environment using a basic unprivileged account |
| Administrator account | Scan Windows systems using administrative credential. |
| SSH Private key | SSH account for our Unix based systems (OSX, Ubuntu, Solaris, HPUX) |
| Profiles | We tested all built-in profiles that ship with NSS 8.0 |
++++
Results
| v : Sucess | x : Failed | * : Not appropriate |
| TARGET | TEST CASES* | RATING | COMMENT | |
|---|---|---|---|---|
| Windows XP Server 1 | Discovery (enumeration...) | x | 5/6 | We remapped some protocols to bind on higher numbers. They had been identified using Full scan. |
| Advanced discovery (full scan..) | v | |||
| Vulnerability mapping | v | |||
| Patch status | v | |||
| Patch deployment | v | |||
| Devices auditing | v | |||
| Windows XP Server 2 | Discovery (enumeration...) | v | 6/6 | Excellent. |
| Advanced discovery (full scan...) | v | |||
| Vulnerability mapping | v | |||
| Patch status | v | |||
| Patch deployment | v | |||
| Devices auditing | v | |||
| Windows Server 2003 | Discovery (enumeration...) | x | 4/6 | Patches related to some outdated software has not been detected. Third part application (Business Object) protocols have not been identified with default profile. |
| Advanced discovery (full scan...) | v | |||
| Vulnerability mapping | v | |||
| Patch status | x | |||
| Patch deployment | v | |||
| Devices auditing | v | |||
| OSX iMacG5 | Discovery (enumeration...) | x | 2/3 | NSS was able to identify (except the OS fingerprint) the most used protocols and some vulnerabilities related to the use of Apache and default SNMP community. “we used the SSH account†|
| Advanced discovery (full scan...) | v | |||
| Vulnerability mapping | v | |||
| Patch status | * | |||
| Patch deployment | * | |||
| Devices auditing | * | |||
| OSX PowerBook G4 | Discovery (enumeration...) | x | 0/3 | NSS wasn’t able to detect the machine. The firewall and stealth mode were activated. |
| Advanced discovery (full scan...) | x | |||
| Vulnerability mapping | x | |||
| Patch status | * | |||
| Patch deployment | * | |||
| Devices auditing | * | |||
| Sun Solaris 8.0 | Discovery (enumeration...) | v | 2,5/3 | The discovery was well performed (hostname, shares, protocols..). However, the Oracle issue was not identified. |
| Advanced discovery (full scan...) | v | |||
| Vulnerability mapping | x | |||
| Patch status | * | |||
| Patch deployment | * | |||
| Devices auditing | * | |||
| HPUX 11.x | Discovery (enumeration...) | x | 0/3 | NSS does not identify filtered protocols due to filtering devices. Nota : the protocol was detected by nmap. |
| Advanced discovery (full scan..) | x | |||
| Vulnerability mapping | x | |||
| Patch status | * | |||
| Patch deployment | * | |||
| Devices auditing | * | |||
| iSeries AS/400 | Discovery (enumeration...) | v | 2/3 | - The OS fingerprint was not correctly identified. - Common protocols has been identified (as well as Telnet, FTP). - Common AS/400 were not correctly identified. - Default username/passwords were have not been identified. |
| Advanced discovery (full scan..) | v | |||
| Vulnerability mapping | x | |||
| Patch status | * | |||
| Patch deployment | * | |||
| Devices auditing | * | |||
| Ubuntu 6.10 | Discovery (enumeration...) | v | 2/3 | - The OS fingerprint was not correctly identified. - Common protocols have been identified (as well as Telnet, FTP…) - Specific Ubuntu security breaches have not been identified |
| Advanced discovery (full scan..) | v | |||
| Vulnerability mapping | x | |||
| Patch status | * | |||
| Patch deployment | * | |||
| Devices auditing | * | |||
| Web site : Security-database.com | Discovery (enumeration...) | x | 0/3 | - We were not able to scan correctly our website (even using the slow networks or playing with scanner options timeout) |
| Advanced discovery (full scan...) | x | |||
| Vulnerability mapping | x | |||
| Patch status | * | |||
| Patch deployment | * | |||
| Devices auditing | * | |||
| Large Windows Network | Discovery (enumeration...) | v | 6/6 | - Excellent and very fast. - Some false positives due to detecting POP3 service. We used administrative privileges for this test. |
| Advanced discovery (full scan..) | v | |||
| Vulnerability mapping | v | |||
| Patch status | v | |||
| Patch deployment | v | |||
| Devices auditing | v | |||
* Test cases include the built-in NSS profiles.
++++
Synthesis
GFI LANGuard NSS is more than an ordinary vulnerabilities scanner. It is by far one of the best software that combines easily a decent security scanner, compliance software (PCI DSS) and patch management tool.
Behind its nice and easy to use interface, GFI LANguard NSS 8.0 uses a strong and flexible security engine. The auditors and security administrators can rely on this product to dress global security view of their network.
IT officers should attest of its strengths to asset systems, deploy necessary patches and hotfixes and report security status trend to their IT dashboards (using GFI ReportCenter).
As final word, there are many advanced features we were not able to check and test. So, open your mind and discover yourself this good software.
For more information about this software and download a trial version visit http://www.gfi.com/languard
GFI LANguard N.S.S 8.0 is recommended for IT Security officers, IT Security Technical Staff and Auditors.
Security-Database gives GFI LANguard Network Security Scanner an overall rating of 4,5/5
Security-Database Rating : |
4,5/5 |
|---|
Attached Pictures
|
Compliance Mandates
|
Related Articles
| Languard NSS |
|
| Network Discovery |
|
| Vulnerability Scanner |
|